Originally published at: https://serversideup.net/how-to-configure-a-wireguard-windows-10-vpn-client/
This post belongs to my “mini-course” on Gain flexibility & increase privacy with Wireguard VPN. I’ll only be walking through how to set up a client for Wireguard on Windows 10. If you don’t have a server (or even if you already have one), definitely start from the top. I make a few assumptions and…
Any way to set a DNS search suffix in this?
Oh… and I should add how much I appreciated you pulling all this information in to one place. It was very helpful.
No problem! Glad I could help @bretmiller. I was just as frustrated as you, so that’s why I did it!
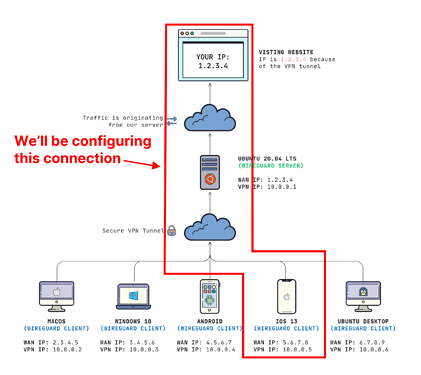
As you are already aware of, I basically focused my efforts on having my Internet traffic route through the server (so I can have a static IP to manage other services):
Looking at my example above, I assume you want the macOS device to be able to communicate with the Windows 10 device through a DNS suffix?
To be honest, I did run into some DNS issues that I got halfway through. If this is what you are looking for, I could do some more tinkering and report back to you.
I’m using it to connect my personal Windows laptop to our corporate office, so was wanting easier access to local servers where we just specify the server name rather than the FQDN. I did eventually find an answer, so here it is in case it helps someone else:
In Registry editor, navigate to
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Tcpip\Parameters
Add a string value named SearchList with a comma-separated list of domains.
Note that this isn’t connection-specific, it’s global. In my case, I’m OK with that. From the GitHub source, it looks like “DNSSearch” will be a config option eventually for the wireguard Windows client and that will be a better solution than making it global for most people.
Thanks for sharing your solution! I’ll probably need this in my next step, so thanks a ton.
I want to create a WireGuard VPN (just like how you are using it – accessing internal systems), but I want to firewall off their access.
Use case:
- Workstations can VPN in from home
- All of their Internet traffic SHOULD NOT be sent over the connection
- Only RDP and possibly local DNS should be sent over the VPN tunnel
- Any other requests over the VPN tunnel will get blocked by the server firewall
Not sure how I am going to do it, but it’s on my list to investigate. 
I haven’t tried to restrict traffic, but I suspect you can do that with the firewall on the server side. Right now I’m having a bit of blocking issue with that so I need to figure out how to enable everything.
As far as restricting which traffic the client sends, here’s my client configuration which should help…
[Interface]
PrivateKey = xxxxxxxxxxxxxxxxxxxxx=
Address = 10.44.1.101/16, fddd:6cdd:d7dd:66dd:44:1:0:101/80
DNS = 10.1.1.2, 10.2.1.2, fddd:6cdd:d7dd:66dd:1::2, fddd:6cdd:d7dd:66dd:2::2
[Peer]
PublicKey = xxxxxxxxxxxxxxxxxxxxx=
AllowedIPs = 10.1.0.0/16, 10.2.0.0/16, fddd:6cdd:d7dd:66dd:1::/80, ffddd:6cdd:d7dd:66dd:2::/80
Endpoint = 1.1.1.1:51820
Hope that helps.
Dear Jay Thanks for the great article!
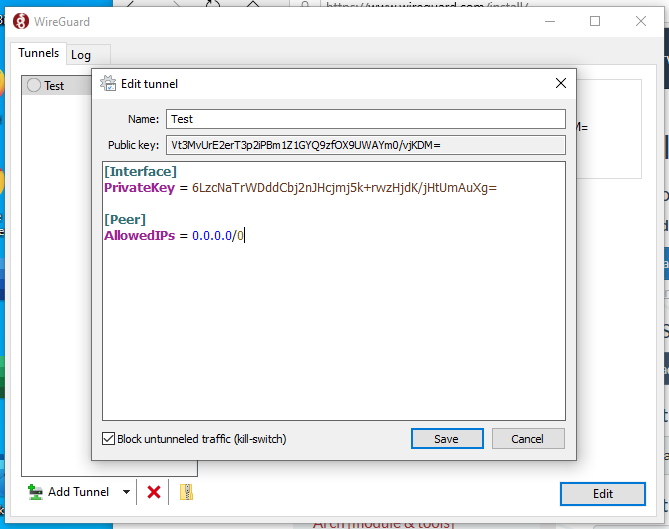
In your article, in “create new tunnel” window there is a “block un-tunneled traffic (kill switch)” checkbox. In fact, one of the screenshot has it but the other other one does not. I have the latest wireguard client application installed (missing the checkbox) on my windows 10 64 bit.
Without that checkbox, I am not able restrict certain traffic to go through vpn tunnel.
If you have any idea please let me know.
Best
Hey @tdpocket!
Sorry for the delayed response, it’s been a busy few days for me. What I learned is the Block untunneled traffic does not appear until you have AllowedIPs in your config file.
I just tested it out and that’s how it worked for me:
Hey @tdpocket,
To further clarify, the checkbox appears only if you route 0.0.0.0/0, not if you selectively route traffic. I created definitions for either, preferring most of the time to route only the essential business network traffic through the tunnel and allow everything else to use the internet connection.
On Windows, if you selectively route traffic, you need to include your local DNS server in the DNS = list or Windows will think there is no internet on either connection.
Yup, you are totally right. Thanks for clarifying @bretmiller!!
Hi Jay, Great write up. I have been running my own OVPN server for a while and decided to set up my own wireguard to try and improve speeds when connected.
I have followed your guide without deviation, but seems that the internet traffic is possibly being blocked.
[Interface]
PrivateKey = REDACTED
Address = 192.168.6.2/24
DNS = 192.168.1.1, 1.1.1.1, 1.0.0.1
[Peer]
PublicKey = REDACTED
AllowedIPs = 0.0.0.0/0
Endpoint = XX.XX.XXX.X:41194
Unsure why it may not be working when i am getting successfully connected.
Hey @eddie563!
It looks like it could be a DNS issue (it’s always DNS, right? ![]() )
)
Check the highlighted area above. Notice how 192.168.1.1 is not on the same network as your Wireguard VPN? That could be an issue because there is no route to 192.168.1.1 when you are connected on VPN.
Try removing that and see if it works (so it looks like this):
DNS = 1.1.1.1, 1.0.0.1
Additional tips
When troubleshooting internet connections, I like to break my troubleshooting into pieces:
1. Is the Internet working without DNS?
I like to ping CloudFlare’s DNS to see if it is responding:
ping 1.1.1.1
2. If the Internet is working, is DNS working?
You can use dig or nslookup to test DNS.
nslookup serversideup.net
Hope this helps! ![]()
Just adding a note on this thread that admin privileges are no longer required for running Wireguard connections from Windows computers. 
This is possible with the latest release of v0.3.1: https://arstechnica.com/gadgets/2020/11/wireguard-for-windows-0-3-1-is-the-release-youve-been-waiting-for/
Hi, could someone post just simple example complete (with real temporary/example key not xxxxx) config file, one on server side and another one on client side ? real example is worth 1000 words ![]()
EDIT:
found it on WireGuard: fast, modern, secure VPN tunnel but there is now Public Key server and client info, and there is different listing port on client side
example, a server computer might have this configuration:
[Interface]
PrivateKey = yAnz5TF+lXXJte14tji3zlMNq+hd2rYUIgJBgB3fBmk=
ListenPort = 51820
[Peer]
PublicKey = xTIBA5rboUvnH4htodjb6e697QjLERt1NAB4mZqp8Dg=
AllowedIPs = 10.192.122.3/32, 10.192.124.1/24
[Peer]
PublicKey = TrMvSoP4jYQlY6RIzBgbssQqY3vxI2Pi+y71lOWWXX0=
AllowedIPs = 10.192.122.4/32, 192.168.0.0/16
[Peer]
PublicKey = gN65BkIKy1eCE9pP1wdc8ROUtkHLF2PfAqYdyYBz6EA=
AllowedIPs = 10.10.10.230/32
And a client computer might have this simpler configuration:
[Interface]
PrivateKey = gI6EdUSYvn8ugXOt8QQD6Yc+JyiZxIhp3GInSWRfWGE=
ListenPort = 21841
[Peer]
PublicKey = HIgo9xNzJMWLKASShiTqIybxZ0U3wGLiUeJ1PKf8ykw=
Endpoint = 192.95.5.69:51820
AllowedIPs = 0.0.0.0/0
Yo pregunto si yo puedo agregarle un proxy a la configuraciòn por que para navegar desde mi empresa necesito poner mi proxy
Unfortunately, I am not aware of any workarounds. If you’re company requires network traffic to travel through their proxy and they block Wireguard, you’ll need to contact your IT staff to have them allow Wireguard for you.
On my mobile now, but ran it into ChatGPT for you. According to it’s partially correct tendencies, it says it’s good ![]()
Are you sure there isn’t another network issue within Starlink that is blocking you? Sometimes ISPs filter based on the packet type.
ChatGPT Response:
The command you provided looks correct for port forwarding with iptables using the WireGuard VPN.
Assuming that the WireGuard VPN is properly configured and running on the VPS and client, and that the IP address 10.1.1.3 is the correct address for the client that you want to forward the port to, this command should forward incoming TCP traffic on port 925 from the VPS’s public IP address to the client at 10.1.1.3 on the same port.
Note that you may also need to configure the client’s firewall to allow incoming traffic on port 925, depending on the client’s network setup.
Oops, I binned my original post as I figured I shouldn’t be hassling others until I did a bit more research. I’ll do some more digging today, and thanks for your reply.
Here’s the OP, restored.
Thanks for this great tutorial. I’ve been able to get it to work fully using a cheap VPS on Vultr.
I’m stuck now with trying to get port forwarding working.
In this example I’m trying to port tcp port 925 from my public (VPS) IP address to the client at 10.1.1.3
iptables -t nat -A PREROUTING -p tcp --dport 925 -j DNAT --to-destination 10.1.1.3:925
No error is visible when giving the command, but it doesn’t seem to work either.
Any suggestions? If not I’ll keep trying and write back when I figure it out.
(All this because of moving to starlink with cg-nat.post deleted by author)
OK so I managed to get it going. I’m not 100% sure of the steps I used, but I did seem to need to edit a rule using ufw. (Actually I tried doing the whole thing within ufw (Uncomplicated FireWall) but it didn’t work.)
-
Edit the
ufwconfiguration file at/etc/default/ufwand setDEFAULT_FORWARD_POLICY="ACCEPT"to allow forwarding of traffic. -
Reload
ufwto apply the new rule:
sudo ufw reload
Apart from that, the rest of it was just adding lines in /etc/wireguard/wg0.conf
PostUp = iptables -A FORWARD -i %i -j ACCEPT; iptables -t nat -A POSTROUTING -o enp1s0 -j MASQUERADE
PostUp = iptables -t nat -A PREROUTING -p tcp --dport 925 -j DNAT --to-destination 10.1.1.3:925
PostDown = iptables -D FORWARD -i %i -j ACCEPT; iptables -t nat -D POSTROUTING -o enp1s0 -j MASQUERADE
PostDown = iptables -t nat -D PREROUTING -p tcp --dport 925 -j DNAT --to-destination 10.1.1.3:925
… and then doing wg-quick down wg0 followed by wg-quick up wg0
Note that most people will have eth0 not enp1s0 (which I found with ip addr command) as I’m running this on a VPS, not a real computer.
So, on Monday I’ll ring Telstra and cancel the ADSL.
@jaydrogers thank you for this insight ![]()