It worked when I did ‘sudo su’ followed by the command. I think that you’re correct about it being to do with redirection. All I have to do now is actually use my Blackview away from home when wifio is available. BTW I did ‘sudo wg set wg0 peer 10.0.0.1’ instead of using 10.0.0.2. I did it again using 10.0.0.2 and it was OK. I’m just wondering if I should unset it for 10.0.0.1. If so, what is the command?
I did this before too and what I did was edit /etc/wireguard/wg0.conf and just delete the peer at the bottom.
Once that was done, I just brought down the interface and brought it back up again.
sudo wg-quick down wg0 && sudo wg-quick up wg0
Hope this works!
I may have got this wrong. But it seems to that the wg0.conf file defines the server interface (which uses, in my case wlp2s0 & 10.0.0.1) and is not connected with the client stuff as specified in ‘sudo wg set CLIENT_PUBLIC_KEY wg0 peer CLIENT_VPN_IP’. Is there a specific file which that command creates or is there a variant of that command to unset the data for an erroneous CLIENT_VPN_IP?
I should have said interface wg0 rather than wlp2s0. I looked at the help for the wg command. It had a remove parameter but it wasn’t of much help. I tried 'sudo wg set wg0 peer 10.0.0.1 but it came up with ‘Invalid argument 10.0.0.1’.
I’m confusing myself: wg0.conf relates to wlp2so rather than wg0…
Did you name your wireguard interface wlp2so?
If not, then wg0 is your wireguard interface (if you followed my instructions at least).
In the beginning of my articles, you’ll find:
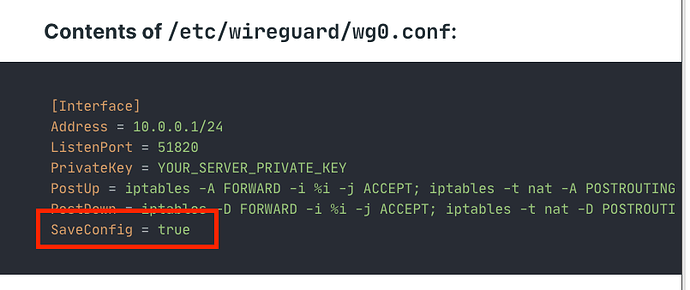
SaveConfig=true
This means that it will write to the file when the interface is brought down.
So before editing that file, bring your interfaces down and up again (you could even reboot just to be safe) and check to see if the peers are written in the /etc/wireguard/wg0.conf file.
Nothing about peers in the wg0.conf file. It’s exactly the same as above.
Referring to my previous message:
But it seems to that the wg0.conf file defines the server interface (which uses, in my case wlp2s0 & 10.0.0.1) and is not connected with the client stuff as specified in ‘sudo wg set CLIENT_PUBLIC_KEY wg0 peer CLIENT_VPN_IP’. Is there a specific file which that command creates or is there a variant of that command to unset the data for an erroneous CLIENT_VPN_IP?
In the example in the step you use eth0 (equivalent of my wlp2s0, mine being wiresless as I have wired not connected and turned off on my server):
[Interface]
Address = 10.0.0.1/24
ListenPort = 51820
PrivateKey = YOUR_SERVER_PRIVATE_KEY
PostUp = iptables -A FORWARD -i %i -j ACCEPT; iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE
PostDown = iptables -D FORWARD -i %i -j ACCEPT; iptables -t nat -D POSTROUTING -o eth0 -j MASQUERADE
SaveConfig = true
As I said before:
I looked at the help for the wg command. It had a remove parameter but it wasn’t of much help. I tried 'sudo wg set wg0 peer 10.0.0.1 but it came up with ‘Invalid argument 10.0.0.1’.
Oh whoops, sorry for the confusion. I understand wlp2so is the replacement for eth0 (not Wireguard’s interface itself).
So this is the weird thing about Wireguard…
Both peers and clients are saved in the same file (on a per interface basis). To my understanding, it saves the peer in memory until you bring the interface down.
Since we have SaveConfig=true in the /etc/wireguard/wg0.conf file. When you bring down the interface (running this command)…
sudo wg-quick down wg0
… it should write your peers to the /etc/wireguard/wg0.conf file.
 Let’s start with this above and see if you can get that far.
Let’s start with this above and see if you can get that far.
One other thing I noticed
If the last config in your message is from your server, I think you have a syntax error. You have eth0 for the “PostUp” and “PostDown”. It should look like this:
[Interface]
Address = 10.0.0.1/24
ListenPort = 51820
PrivateKey = YOUR_SERVER_PRIVATE_KEY
PostUp = iptables -A FORWARD -i %i -j ACCEPT; iptables -t nat -A POSTROUTING -o wlp2s0 -j MASQUERADE
PostDown = iptables -D FORWARD -i %i -j ACCEPT; iptables -t nat -D POSTROUTING -o wlp2s0 -j MASQUERADE
SaveConfig = true
If you have further issue:
- Can you confirm you brought your interfaces down and up again?
- Can you reboot your server just to be safe?
- Can you post your
wg0.conffile using proper code formatting? This will help me out a ton in helping you faster. (Hide your keys, of course)
Brought wg0 interface down & up again, using wg-quick.
Rebooted Xubuntu (i.e. PC with WireGuard).
Here is contents of wg0.conf without formatting:
[Interface]
Address = 10.0.0.1/24
SaveConfig = true
PostUp = iptables -A FORWARD -i %i -j ACCEPT; iptables -t nat -A POSTROUTING -o wlp2s0 -j MASQUERADE
PostDown = iptables -D FORWARD -i %i -j ACCEPT; iptables -t nat -D POSTROUTING -o wlp2s0 -j MASQUERADE
ListenPort = 51820
PrivateKey = *********************************
Here it is with 3 backticks before & after:
Address = 10.0.0.1/24
SaveConfig = true
PostUp = iptables -A FORWARD -i %i -j ACCEPT; iptables -t nat -A POSTROUTING -o wlp2s0 -j MASQUERADE
PostDown = iptables -D FORWARD -i %i -j ACCEPT; iptables -t nat -D POSTROUTING -o wlp2s0 -j MASQUERADE
ListenPort = 51820
PrivateKey = *********************************```
Thus, no change from original wg0.conf after above steps.Thanks for running through those steps! Still strange that it’s not working…
I found this helpful discussion: https://www.reddit.com/r/WireGuard/comments/f3ihmx/confused_about_server_configuration_workflow/
What happens when you run wg-quick save on the wireguard server after you add your peer? Does it write it to the file then?
Jay,
When I ran ‘sudo wg-quick save wg0’ (wg0 is required as it gave error without it) and checked /etc/wireguard/wg0.conf a new section starting with [peer] as per your guide was created. Hurrah! I suggest adding that command to your guide.
BTW I suggest adding links for each part of guide at the bottom of each part. This would then allow going backwards to check that one has done a part correctly. These little things make a tutorial much easier to understand. I used to write a lot of User Guides/Manuals when I was a Business Analyst & Systems Analyst before I retired to become a BOF!
When I follow tutorials written by SysAdmins etc, I copy the resultant files to my home directory changing permissions to myself if created by root (which I later backup to the cloud using DropBox) so as to have an easy to refer to future reference (partly because I never remember, perhaps due to my memory getting worse, which conf & key files etc the system has created from my commands).
Hey @JohnAaronRose,
Thanks for letting me know! Sorry for the delay on getting back to you, it’s been a busy week.
Thanks for the feedback! Out of curiosity, did you notice these at all? Or do you mean links within the blog post?
I didn’t notice them. I think that I assumed that they were for other tutorials. I’m also used to looking at the bottom of a page for previous & next sections.